How to set up a gitea docker instance
Basic installation
To setup a gitea server using docker, the following docker-compose.yml file shall be used:
networks:
gitea:
external: false
services:
web:
image: gitea/gitea:latest
environment:
- USER_UID=1002
- USER_GID=1002
volumes:
- ./data:/data
- /home/git/.ssh/:/data/git/.ssh
ports:
- "3000:3000"
- "2200:22"
depends_on:
- db
restart: always
networks:
- gitea
db:
image: mariadb
restart: always
environment:
- MYSQL_ROOT_PASSWORD=<redacted>
- MYSQL_DATABASE=gitea
- MYSQL_USER=gitea
- MYSQL_PASSWORD=<redacted>
volumes:
- ./db/:/var/lib/mysql
networks:
- gitea
What the above docker-compose configuration will do is that it will, in essence, create two, always on, services, that will forever be restarted: a mariadb database server that will write all of its data to a local "db" directory, and another web service that will server as the main git server and the web server alongside it.
Before starting the docker services, please create the necessary resources first.
Create the required local directories to store the data in
Do a simple command to create the necessary directories:
mkdir data db
Backing up just these two directories should, in theory, be enough to allow for full restoration of all git repository resources into the future. WARNING: This has not been tested yet!!!
Create a separate git user to login into via SSH
Creating a separate user, technically, is unnecessary, but it makes the configuration more conventional.
Assuming the 1002 UID is already assigned to a different user, feel free to use a different UID (be sure to update the yaml configuration with the proper user ID, then).
Once this configuration has been done, go ahead and generate an /home/git/.ssh/ directory for the user to have. Be sure to chown this specific directory to the git user as appropriate:
chmod 700 /home/git/.ssh/
Once all these steps are done, you can proceed to the next step.
Spin up a container from the docker image
Had all the necessary steps been done properly, this should yield a fully functional container. If there are any errors encountered by this point, please fix them before proceeding.
Set up a proper nginx endpoint for the docker service
Deploy the following configuration to make the container accessible to the outside world:
server_name git.transistor.one;
listen [::]:443 http2 ssl; # managed by Certbot
listen 443 http2 ssl; # managed by Certbot
# http2 on;
include /etc/nginx/snippets/ssl.conf;
location / {
proxy_pass http://localhost:3000;
}
}
Once this is done, restart nginx:
Confirm that the web page is accessible at the git.transistor.one URL. In case it's not, fix it.
# Customize Gitea configuration #
Assuming you do need to change a couple of settings, gitea will have generated a configuration file at ./data/gitea/conf/app.ini.
Make whatever changes you need to make in this file.
The changes will take effect only after stopping and restarting the container, though.
Notable changes that are worth mentioning is setting up an SMTP endpoint:
ENABLED = true
PROTOCOL = smtp+starttls
HOST = mail.transistor.one:587
FROM = gitea@transistor.one
USER =
PASSWD =
And, of course, the server hostname configuration:
APP_DATA_PATH = /data/gitea
DOMAIN = transistor.one
SSH_DOMAIN = transistor.one
HTTP_PORT = 3000
ROOT_URL = https://git.transistor.one/
DISABLE_SSH = false
SSH_PORT = 22
SSH_LISTEN_PORT = 22
Oh and, almost forgot, disable user registrations by setting
DISABLE_REGISTRATION = true
If you need more configuration information, check this out.
Activating SSH passthrough
This is the most complex step out of all of them. In order to take advantage of the fact that SSH git pulls/pushes will be done via standard port 22, normal SSH traffic needs to be differentiated from git specific SSH traffic.
To this end, multiple configurations will need to be done.
This one's extremely important. Failing to perform this step will make SSH git pulls and pushes require to be done directly from the 2200 port like so
While this isn't the end of the world, ideally, all SSH traffic should be routed to port 22, as is standard. VPS firewalls or intermediary ISPs may, themselves, block off incoming or outgoing traffic to unconventional ports, which can cause issues. As such, using the standard port 22 for SSH communication would be ideal.
Enable SSH login for the git user
So, to enable SSH capabilities to the git user, please edit the "/etc/ssh/sshd_config" configuration and change the following line:
Obviously the "alex" user doesn't need to be here. The git user does. Change this list as best suits your needs. Don't forget to restart the service after you're done:
Generate a proper public/private keypair for all the accounts that need to use git via SSH with
This part's pretty self explanatory.
For each user, on each device, that will require SSH git access to the aforementioned git server, they will need to have their own public/private authentication keypair set under a Gitea user that's already registered on the Gitea web portal.
Check to see if a public/private keypair doesn't already exist under your user's /home/<username>/.ssh/ directory. You'll recognize already existent keypairs by the presence, in this directory, of <name>.pub files. If you already have at least one such file already there, copy the contents of the <name>.pub file to the clipboard and add it to your Gitea user's settings. In case there is no such .pub file already existent, you'll have to manually generate ones for yourself.
To do so, simply log into each user and run from the terminal:
That's pretty much it. Once you generated a keypair, again, visit the /home/<username>/.ssh/ directory and check for <name>.pub files. There should be at least one there, now.
Copy its contents and add it to your Gitea's user settings through the web interface, as follows:
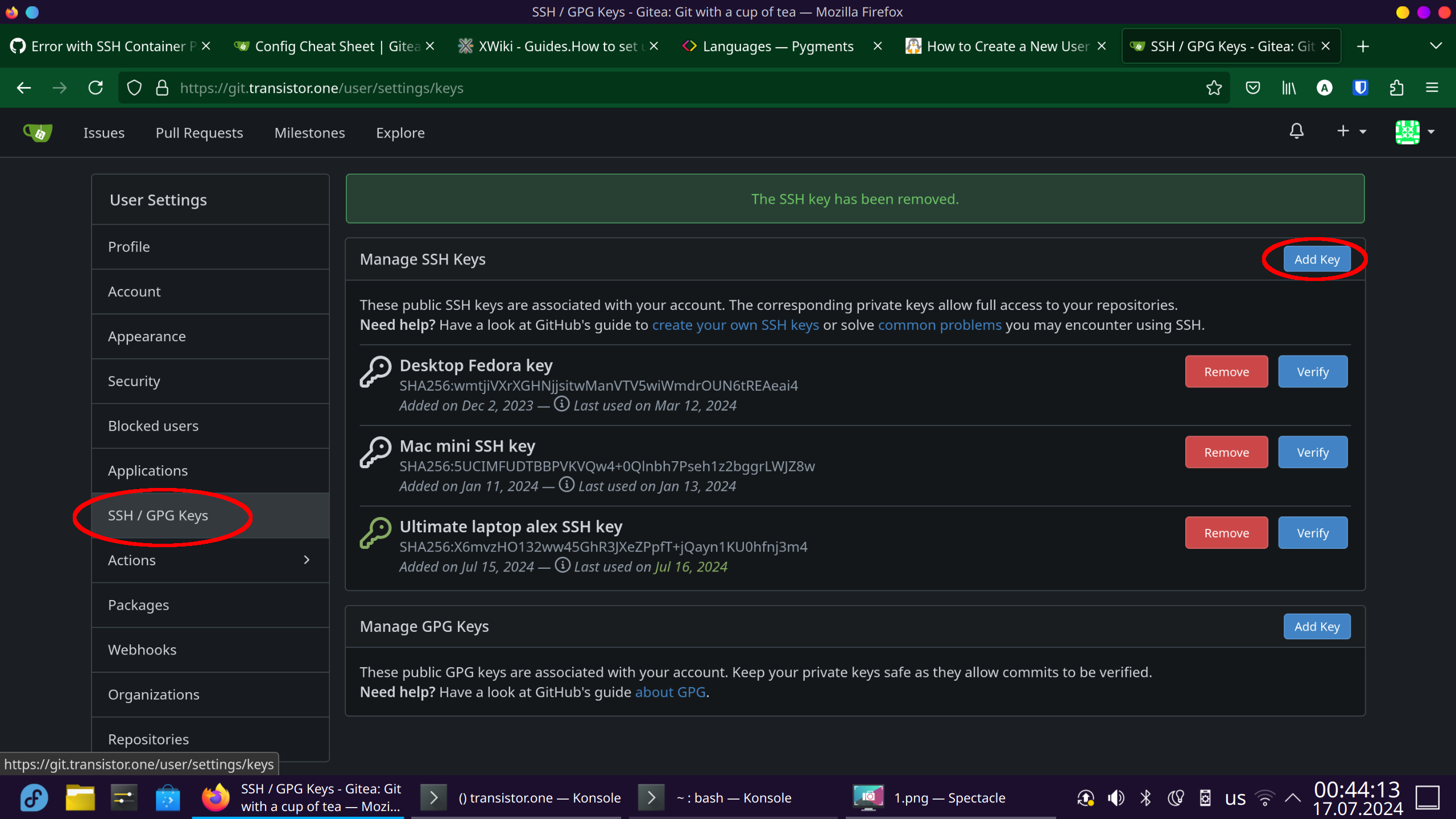
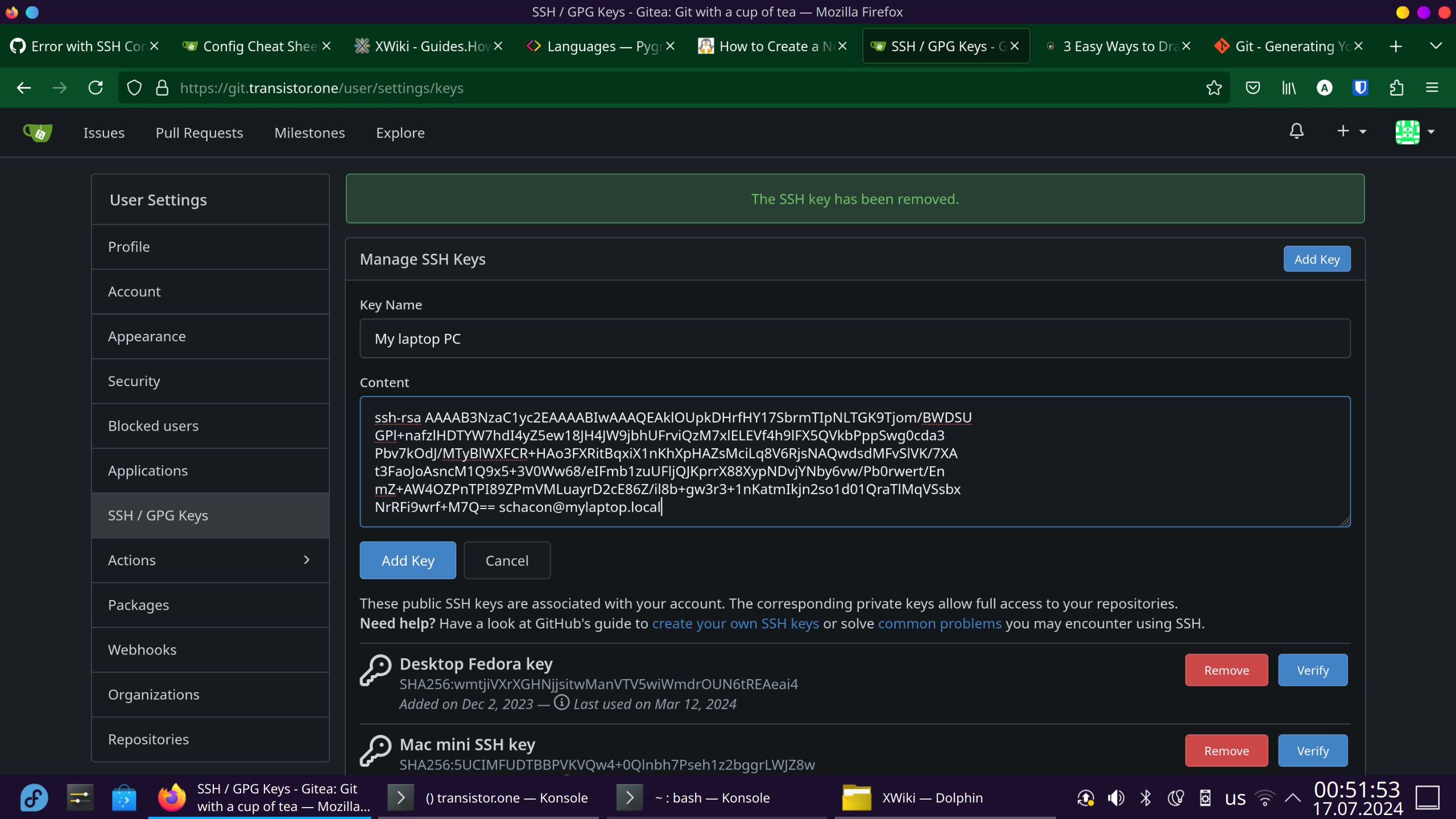
Once the public key is registered here, you should be able to do git push and git pull from this particular repository using SSH, without the need for further authentication. However, there's still a couple more steps left to follow:
Generate a public/private keypair for the git user as well
This might not be immediately obvious why this is necessary, but in order for the SSH passthrough to work, the git user that we'll log into in the future will have to forward all SSH requests to inside the docker container. In order to do so, the container's own SSH server will need to recognize the requests as authenticated from the git user on the host machine.
To this end, we will have to generate a keypair for the git user as well:
Once this part is done register the newly generated public key to the SSH server inside the docker container, by appending it to the /home/git/.ssh/authorized_keys files inside the host.
To do so, please do:
sudo -u git chmod 600 /home/git/.ssh/authorized_keys
You might wonder why we're changing a file on the host filesystem and not inside the docker, where the relevant SSH service is running. The reason for this is, remember, this particular directory is already mapped in our docker-compose.yml file, so it exists in both the host machine and in the docker container, simultaneously. All changes that take place to it on the host will reflect inside the container.
Please do note that registering the git user's public key has to be done using the above commands AND NOT THROUGH THE WEB INTERFACE, LIKE IN THE PREVIOUS STEP (I already lost 2 days investigating why this thing didn't work because I didn't pay attention to this step)
Write an SSH Shim script
Here, we'll need to generate a script at "/usr/local/bin/gitea" owned by root:root and with chmod 755 with the following contents:
ssh -p 2200 -o StrictHostKeyChecking=no git@127.0.0.1 "SSH_ORIGINAL_COMMAND=\"$SSH_ORIGINAL_COMMAND\" $0 $@"
This script might seem confusing, at first glance, especially since there's another, entirely different "/usr/local/bin/gitea" script that exists in the docker container.
The script above will simply forward all incoming SSH connections that originally came to the host server and sends them to the docker container (specifically to localhost port 2200 which, according to the yaml file above, is mapped to port 22 inside the container). There, the container will run the command that was originally sent to the host machine inside of itself and return the result to the original outside client.
You may be thinking "But how does the host SSH server know when to run this script to forward requests inside the container and when not to forward requests?". Basically, this is done via the /home/git/.ssh/authorized_keys file.
When we added all those public keys at this step, the Gitea webserver appended those public keys to the /home/git/.ssh/authorized_keys file that is already mapped into the container. Those keys are written with a special
"command="/usr/local/bin/gitea --config=/data/gitea/conf/app.ini serv key-9",no-port-forwarding,no-X11-forwarding,no-agent-forwarding,no-pty,no-user-rc,restrict ssh-ed25519 AAAAC...."
prefix, which basically tells the SSH server running on the host that, whenever an SSH client that authenticates itself with a matching public key from this format, connects, then the command that this client sent us is saved in an SSH_ORIGINAL_COMMAND environment variable and the command after the "=" symbol gets automatically executed by the SSH server. In our case, this will run the "/usr/local/bin/gitea" shim script from the host machine which we already created in this step, which in turn will forward that command to inside the docker container to be ultimately handled.
Of note is the fact that entries inside the "/home/git/.ssh/authorized_keys" file which don't start with the "command=" format that the Gitea web server saves its entries under, will simply login as normal via SSH.
We're done
The server is officially running. Happy coding!